IPv6-first debian server
Posted
I’ve been wanting to self-host and implement remark42 comment system on this website for a while. I recently decided to take the plunge and since I was doing it anyway, I figured that I might as well setup and be ready for the future, which I’m told is IPv6.
Out of all the options in self hosting, renting a VPS (Virtual Private Server) was the most appealing to me. For my hobby projects, I imagined I could get a shared server and host multiple projects on the same server, just on different ports using a reverse proxy.
To implement this, I was initially looking at DigitalOcean droplets but then came across hetzner
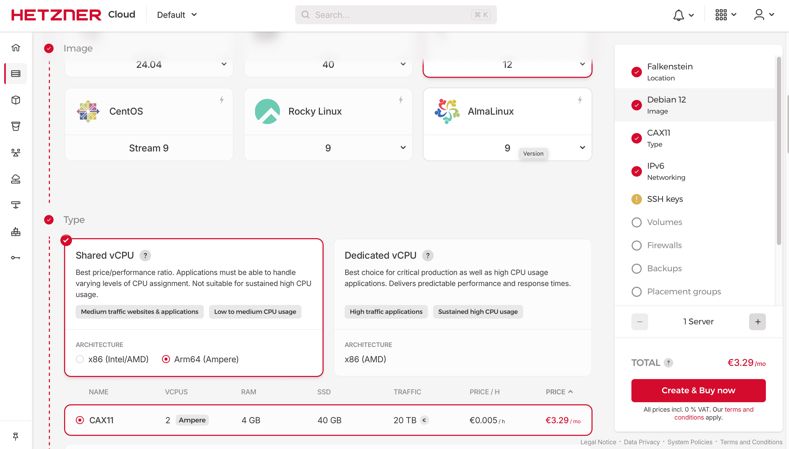
which provided much better options as opposed to the former. For example the cheapest droplet came at 4$ a month and gave 1vcpu, 500MB ram, 10GB ssd storage while hetzner came at 4.11$(Converted from Euros) a month and gave 2vcpu, 4GB ram, 40GB ssd storage and you have an option to choose the architecture between x86 and Arm64 in hetzner.
So, it was an easy choice.
On top of this, hetzner have been operating their datacenters in germany and finland entirely using 100% green electricity apparently. It was refreshing to see their sustainability page .
I read online that it was a bit tough to get approved by hetzner though, especially if you are from India. I didn’t face any issues but here is a tip I came across that helped:
Use a custom email address attached to your domain as opposed to a generic gmail address.
It apparently helps you stand apart from all the bad actors out there. You can also:
Use icloud+ to create personalised email addresses for free if you already have a domain
I’ve had this domain for a while, so I used my already existing icloud+ subscription and created personalised email-ids and used one of them to create an account.
Setting up the Server
Create server
While creating the server, I chose Debain 12 as I wanted something lightweight and no-nonsense. In the networking section, I only selected IPv6 in the networking section for to be IPv6 first. If needed, I could get an IPv4 address anytime later on.
Setup firewalls
For setting up the firewall, I read about a computing concept called Defence in Depth and the idea is (if possible) to have multiple layers of security.
-
With Hetzner, it was possible to setup a “Network Firewall” which I figured could be the independent first layer
-
Inside the server, it was possible to setup the uncomplicated firewall (
ufw) which is a frontend for iptables and is a “Host based Firewall” which could be the independent second layer
Now, both 1. and 2. are mutually exclusive and need to be setup separately. This means troubleshooting connectivity issues will be more difficult but it also means we have redundancy in the event a vulnerability is exploited in one of the layers.
To setup the ufw firewall first, after ssh-ing into the server, you wanna run
$ apt update -y
$ apt upgrade -y
$ apt install ufw
$ ufw default deny incoming
$ ufw default deny outgoing
The above commands install ufw, and set the default to denying all incoming and outgoing connections
$ ufw allow 22/tcp
$ ufw allow 80
$ ufw allow 443
Port 22 is generally used for ssh. So we will allow that (We will setup fail2ban later, so we set ufw policy
to allow and not limit). Port 80 is HTTP and port 443 is for HTTPS
$ ufw allow out 80
$ ufw allow out 443
$ ufw allow out 53
We need to set outgoing DNS port 53 open and outgoing HTTP and HTTPS ports i.e. 80 and 443 OUT ports enabled in order to have apt-get function properly.
$ ufw enable
$ ufw status
Finally, we enable and check the status.
The same firewall rules are to be applied on the UI side of hetzner:
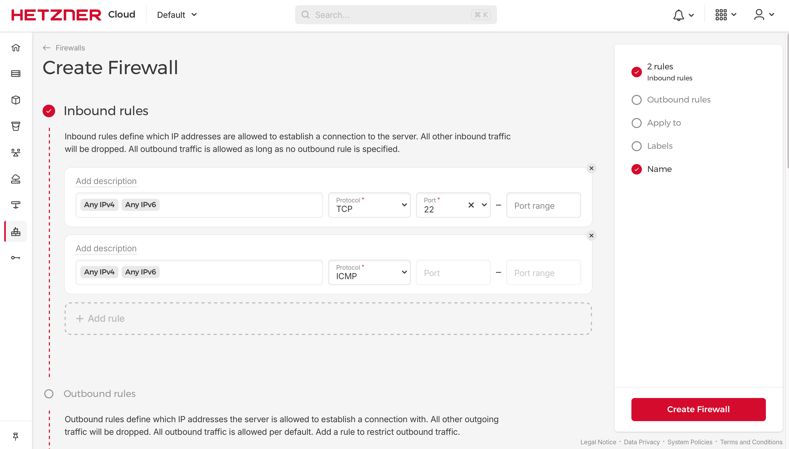
And we have two layers of firewall setup!
Setup fail2ban on debian
Fail2ban is a daemon that scans log files like /var/log/auth.log of services and ban clients that repeatedly fail authentication checks. It does this by updating system firewall rules to reject new connections from those IP addresses. Also, since it uses the same firewall structure managed by ufw, it adds no additional load to the server.
apt update -yapt intall fail2ban- Go into
/etc/fail2banand make copies of 2 important config files because if we update the package, fail2ban won’t touch the copies and will only update these conf files. We can use them as reference and still alter our settings as we want. - To do so,
$ cp fail2ban.conf fail2ban.local
$ cp fail2ban.conf jail.conf jail.local
- Look at this video for more context for how jails work and what settings to setup
- Now most important to setup is the sshd jail. Turns out it has some issues when directly being installed. You can check that when you run
fail2ban-client statusif you are hit with:
ERROR Failed to access socket path: /var/run/fail2ban/fail2ban.sock. Is fail2ban running?`
Now if you see this, then you’ve to make some changes to the jail.local file.
[sshd]
enabled = true
filter = sshd
port = ssh
logpath = /etc/fail2ban/sshd_jail_log
backend = auto
- Create an empty file called
sshd_jail_loginside/etc/fail2banfor the log. - I also had a warning about IPv6 which being set to auto by default. This was rectified by just editing it in the
fail2ban.localfile where just uncomment and setallowipv6 = yes - Now you might want to run
sudo service fail2ban startand checkfail2ban-client statusagain and sshd jail should be running.
Final thoughts
As I am writing this, I have already setup remark42 on my website, and I managed to do it purely with an IPv6 address. But it was almost funny how much gymnastics it took.
For example: I was trying to clone a repo from Github when I got to know they still doesn’t support IPv6 in 2024! I had to find a tedius workaround. ( Btw here’s a nifty website to check: isgithubipv6.live
)
Another example: How do I get my firebase app to use IPv6?? Nothing in the docs but after searching for a bit I found a great post that helped me set it up.
Anyway, after many more problems and solutions, I finally hit a dead end when I wanted to host an SMTP server. It is sad to say that even in 2024, it is near impossible to run an IPv6 only server. Let’s try again after a decade I guess, but hopefully, the internet catches up sooner.